Cryptocurrency Scam: How to Spot and Avoid Them
When dealing with Cryptocurrency Scam, a fraudulent scheme that tricks people into sending crypto or revealing private keys. Also known as crypto fraud, it thrives on the hype around digital assets and the speed of online transactions.
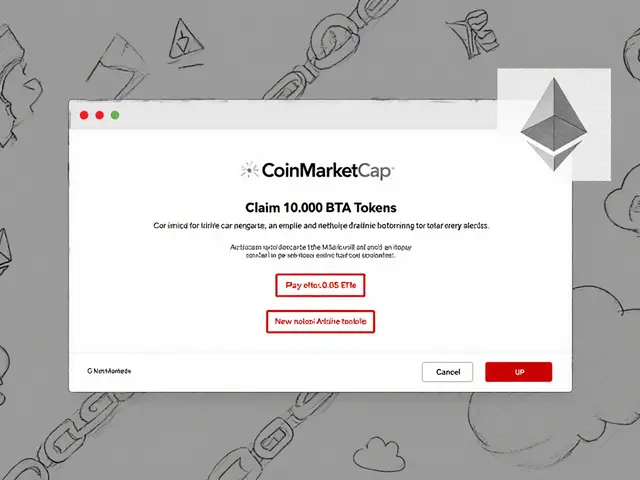
One of the most common tricks is a Phishing Attack, an email or message that mimics a legit service to steal login credentials. Phishing attacks cryptocurrency scam actors use to gain immediate access to wallets. By recognizing fake URLs, misspelled domains, and urgent language, you cut the attacker’s path to your funds.
Typical Fraud Patterns You Should Know
Another big player in the fraud world is the Ponzi Scheme, a promise of high returns that pays early investors with money from later ones. Ponzi schemes create the illusion of profit, urging you to reinvest or recruit friends. The scheme collapses once new money dries up, leaving most participants with losses.
Rug pulls are a newer, blockchain‑specific danger. In a rug pull, developers launch a token, hype it, then withdraw all liquidity from the pool, making the token worthless. This tactic exploits the trustless nature of DeFi platforms, where code runs automatically without a central authority to intervene.
Fake ICOs (Initial Coin Offerings) also keep the scam ecosystem alive. They present a polished whitepaper, professional website, and sometimes even celebrity endorsements, but the token never materializes or is a total dump after the sale. Investors lose money because the promised product never launches.
All these fraud types share a core requirement: they rely on social engineering, misinformation, and the anonymity of crypto networks. Understanding how each method works helps you build a mental checklist before you click, sign, or send any coin.
To protect yourself, start with basic hygiene: use hardware wallets, enable two‑factor authentication, and verify contract addresses on official sources. Keep an eye on community signals—sudden price spikes, unverified claims, or pressure to act quickly are red flags.
With these insights, you’re ready to explore the detailed articles below. They break down real‑world examples, show how to investigate suspicious projects, and give step‑by‑step actions to keep your crypto safe.
OnBlock Exchange Review: Is This Crypto Exchange Legit or a Scam?
A thorough look at OnBlock Exchange, its missing credentials, red flags, and how to verify any crypto platform before you trust your funds.
View More